Cyber Security for OT
For years cyber security in the OT space was an afterthought. With the emergence of Smart Buildings, remote access, and more data being shared on an OT network, the need to secure these networks has become critical. Products and solutions that are OT-focused tend to address network security needs with broad IoT solutions. Although best-in-class product selection is vital when choosing your hardware and software, most security breaches are caused by lack of knowledge by the user. It is highly recommended that a written cyber security plan is developed and followed in order to provide proper network security training for all users.
Four Areas of Cyber Security for OT Networks
Play the video below and listen as we explain our basic approach to ensuring that your OT network design is cyber secure. It is crucial that you follow a few basic best practices so that your data and assets are protected from cyber threats.
- Area 1: Encrypted Data (Tridium's Niagara/BACnet SC)
- Area 2: Managed Network Switches
- Area 3: Physical Firewall
- Area 4: A Written Cyber Security Policy
Cyber Security Policy Guide Specification
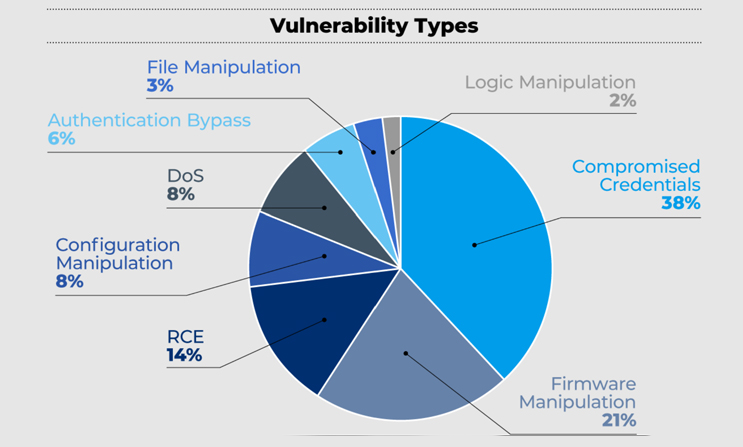
OT cyber security management is a continuous process with all types of factors influencing the results. Changes in business demands, organizational changes and changes in the threat landscape all require adaption of the OT cyber security management process. A good cyber security plan is an excellent place to start. This document is merely a starting point and is considered a guide specification. The document should be edited by the owner before being adopted by your organization.
How We Approach Cyber Security for Your Project
Here is a behind-the-scenes look at the collaborative effort required to define and implement an OT network and Cyber Security Plan for a municipal project. Many aspects are discussed including software and hardware security, readiness and disaster recovery, and the often-overlooked access control. The famous phrase, “It is a process, not an event” is exemplified through examining the methodologies used. Where do the boundaries of IT/OT convergence and divergence meet? Where do the elements of physical security fit into the scenario? What are the simple rules to follow when your system has been compromised by a vulnerability? The answers are discussed in this series of short, entertaining videos.
Playlist
Cyber Security Tips for OT from Around the Industry
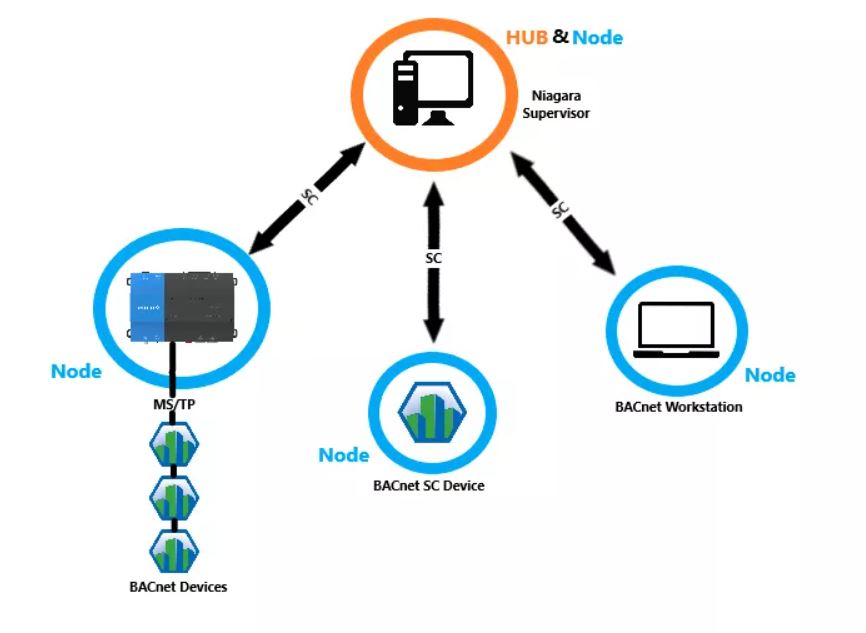
BACnet Secure Connect (BACnet/SC)
BACnet/SC is a new BACnet datalink that eliminates many of the concerns Owners, Facility Managers, and IT professionals have with BACnet today. It is based on standard TLS 1.3 security with options for 128-bit. and 256-bit elliptic curve cryptography. It eliminates the need for static IP addresses. Information sent through a BACnet/SC connection is verified to be authentic, and unaltered from the original data source. BACnet Secure Connect (BACnet/SC) is an addendum to the BACnet protocol released by the ASHRAE BACnet Committee.